When we think of criminals, usually you think of the masked robber or the terrifying-looking man with a knife. It was fairly easy to avoid these people with standard safety practices, but now a new danger has emerged that is not as easy to identify and not as easy to avoid. We now have to worry about criminals who could be on the other side of the planet, hiding in plain sight or disguised as something innocuous. Cybercrime is growing as an international issue since the creation of the internet. In fact, according to Forbes, damages from cyber crimes are predicted to have cost the global economy over $2 trillion in 2019.
Today, computer viruses and other malicious software programs are no longer developed by amateur hackers who seek fame and glory within their social groups. Most cyber-attacks are orchestrated by professional criminals who can earn millions with their attacks. These criminals want access to our computers, our PayPal passwords, and our credit card numbers, anything that will help them gain infamy and monetary gains.
Cybercrime is becoming more and more prevalent with criminals figuring out new and creative ways to get what they want and cybersecurity experts are struggling to fight back. With that being said, let us look at some of the cyber attacks that have gone down in infamy.
10 Worst Cyber Attacks in History
Morris Worm
The Morris Worm is one of the first computer viruses in history. It was created by university student Robert Morris, to whom he gave his name, and spread via the Internet (then ARPANET) on November 2, 1988.
The objective of this attack was to obtain the passwords of other computers taking advantage of some defects in the Unix version of the University of Berkeley.

Source: HERE
The Morris worm was the first self-replicating malware, designed to reproduce itself indefinitely instead of deleting data. It affected about 6,000 of the 60,000 servers connected to the network, including the NASA research centre, leaving some of them almost useless.
Although it was not programmed to cause damage, the effects of the attack were catastrophic for the moment: it produced failures in the computers of universities, government agencies, and companies. Eradicating it cost almost a million dollars, and it is estimated that it caused losses of $96 million, very high figures for the time.
ILOVEYOU
The ILOVEYOU worm spread like wildfire in the month of May of the year 2000. It used an email with the title “LOVE-LETTER-FOR-YOU” causing people to open the email. Once opened the worm would replicate itself and the forward itself to each contact in the victim’s address book. Once on a victims computer the virus, downloaded a password-stealing application programmed to send their passwords to the hacker and replaced multiple files with copies of itself.
It is believed that it infected 55 million computers worldwide, causing more than 10 billion dollars in losses.
Code Red
Code Red is another of the worst attacks ever. This worm, which was discovered in July 2001, exploited a very common vulnerability known as a buffer overflow, using a long string of characters to overflow the buffer and collapse the server. Computers with the Code Red worm gave hackers a back door into their computers.
The Code Red worm achieved great notoriety at the time because it collapsed all the White House web servers through a DDoS attack. The virus infected more than 225,000 systems worldwide and resulted in losses of more than 1.2 billion dollars.
Mirai
A botnet infected computers without security and started to spread on a massive scale. The devices tracked down more of the same type of devices and continued for years to spread the botnet. The computers all contained malware called Mirai (Japanese for future). In October 2016, the owners of the botnet decided to test out what they could do. The botnet was in millions of digital video recorders, routers, IP cameras, and other smart devices, all which flooded the DNS service provider Dyn with requests. Dyn could not process the number of requests and went out of operation.
Companies such as PayPal, Twitter, Netflix, Spotify, Playstation and many other platforms that host on DNS were not accessible. The server eventually came back online but not without sending a serious warning for products that were previously thought unhackable.
Storm Worm
Another of the most fearsome viruses in history is Storm Worm, a worm that began to spread by email in early 2007. The malware gets its name from the subject that used the email “230 dead as storm batters Europe”.
The Storm worm is a Trojan with different versions for Windows computers that aimed to add infected computers to the Storm botnet. It’s estimated that in September 2007, it had between 1 and 10 million zombie computers and has been used to perpetuate various criminal activities.
In subsequent years, this virus has been used on a recurring basis by modifying the issue to show current news.
For example, before the celebration of the Olympic Games in China, a new version was propagated using catastrophes allegedly occurring in the Asian country as a hook.
Conficker
In October 2008, another disastrous cyber attack took place, in this case starring the Conficker worm.
Source: HERE
This malware exploited a Windows Server vulnerability on Windows 2000, Windows XP, Windows Vista, Windows Server 2003, and Windows Server 2008 systems, and once it had infected a computer, it deactivated several services, including Windows Automatic Update. The worm then received instructions from a C&C server, including the theft of personal data and self-propagation.
It is estimated that Conficker infected up to 15 million computers worldwide and caused damages valued at $9.1 billion.
PlayStation Network Attack
The tech giant Sony was not saved from cybercriminals and was one of the first major technology corporations to be targeted in a mass attack. In April 2011, the Japanese multinational announced that some functions of the PlayStation Network had been violated.
This caused the PlayStation online service to be affected for almost a month, so 77 million users were left without online access to the PSN for 23 days, costing the company approximately 180 million dollars.
Months later, the company appeared before the United States House of Representatives and was sentenced to pay a fine for $324,000 to the ICO ( Information Commissioner's Office ) of the British government for its weak computer security measures.
This series of massive attacks on personal information is only a clear example of the danger of not adequately protecting corporate networks with Internet access. Therefore, it is necessary for companies to take the corresponding preventive measures and make timely management of their information.
Stuxnet
In June 2010, the Belarusian security company VirusBlokAda discovered the Stuxnet virus, a worm capable of spying and reprogramming industrial systems, designed to target Iranian nuclear centrifuges. These centrifuges would spin out of control and destroy themselves before the monitoring systems could figure out what’s wrong
It was the most sophisticated virus at the time, with its ability to reprogram and even destroy infected computers, causing serious damage. It was never meant to leave the Natanz nuclear enrichment facility. However, due to its aggressive nature, it spread to other computers in the wild.
What’s really interesting about the virus is the fact that it was able to get into “air-gapped” computers, which are computers that are not connected to the internet. Air gapped computers were attacked by USB thumb drives that unknowingly were infected with the virus uploading the worm.
ZeuS
In September 2011, ZeuS, a malware that spread through phishing campaigns was launched. After infecting a device, ZeuS was able to intercept the victim's bank transactions and copy their login credentials.
Based on the ZeuS Trojan, the GameOver ZeuS botnet was born. Its distinctive feature is that it used P2P type communications to control zombie computers remotely. The main operating systems he attacked were Windows XP, Windows Vista, Windows 7, Windows 8.
Source: HERE
Experts estimate that the GameOver ZeuS botnet was comprised of between 500,000 and 1 million zombie teams, and the FBI believes it was responsible for more than $100 million in losses.
Carbanak
Carbanak is an APT (Advanced persistent threat or advanced persistent threat) campaign directed against financial institutions that began to attack in 2014.
The attack began when criminals managed to infiltrate the bank's intranet through fraudulent emails. Later, the malware was able to take control of the computer, and the group of hackers used it as an access point to the entity.
Next, hackers analyzed the financial tools used by the bank, and then withdrew money by transferring SWIFT money or creating fake bank accounts.
Through this malware, cybercriminals managed to steal about $1 billion from more than 100 financial institutions in about 40 different countries.
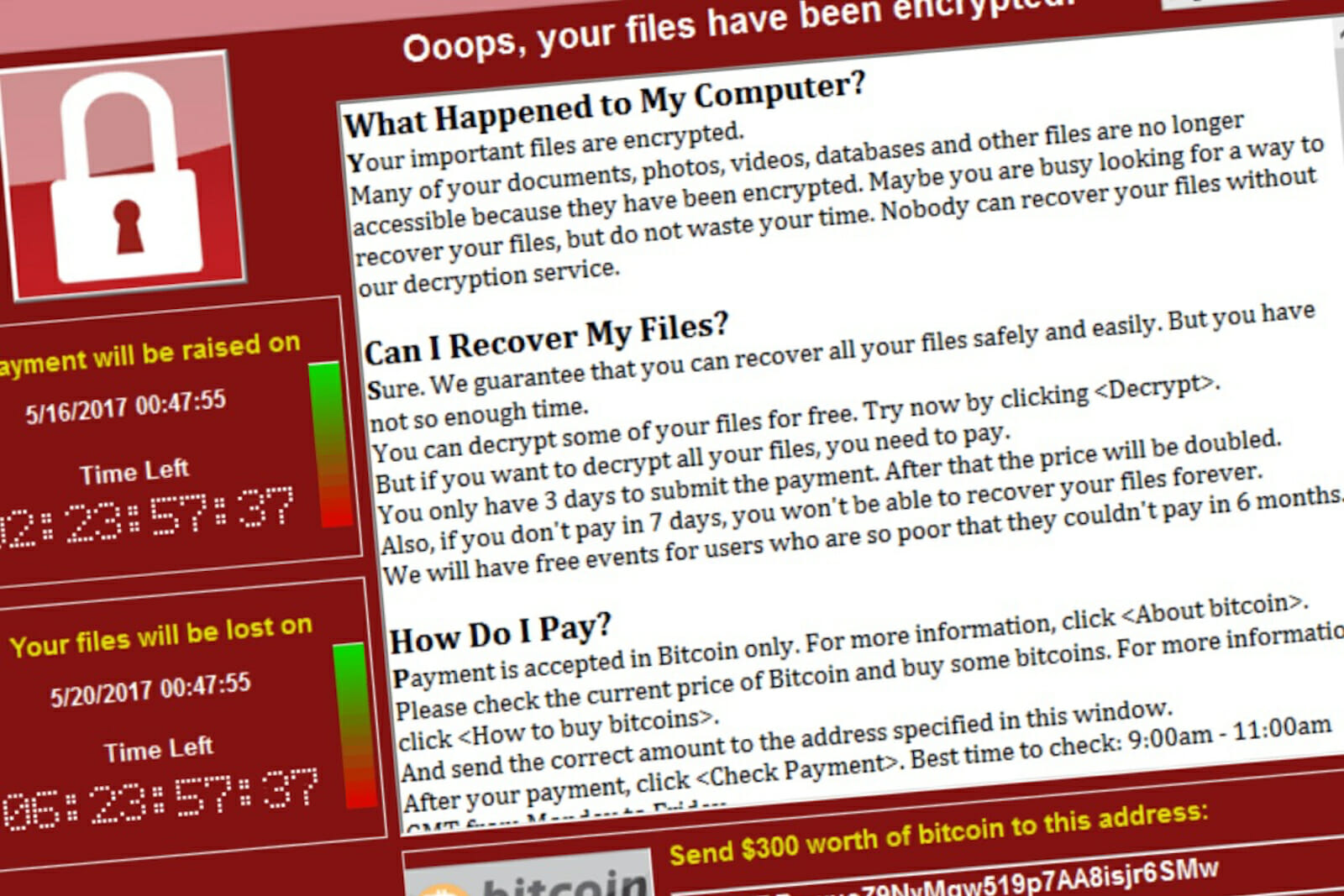
WannaCry
Without a doubt, the WannaCry ransomware has been one of the worst cyberattacks in history and the most important of the current era, whose losses, scope and repercussions have been a before and after in the world of cybersecurity.
WannaCry spread on May 12, 2017, and not only managed to paralyze thousands of companies around the world but also showed how fragile the system could be in the face of certain attacks.
Source: HERE
As you will remember, the malware was able to hijack a computer by encrypting all its files and blocking the access of the administrator and other users. To return control of the equipment, as other ransomware asked for the payment of a ransom.
According to Deloitte's study, " What impact has the WannaCry cyber incident had on our economy? " The WannaCry ransomware affected more than 360,000 computers in 150 countries. The attack caused direct losses of over $200 million worldwide, to which we must add indirect losses and other costs. To date, its losses amount to $4 billion.
The lethal and innovative cyberattack of NotPetya
As if it were an epidemic, once again, malware attacked and managed to knock down governments and multinationals, making it appear that the WannaCry was just a small attack. Initially, the malware in question was identified as a variation of the ransomware called Petya. However, after a more thorough analysis, most experts agree that it is a qualitatively different virus, although it has reused much of the code of Petya.
One of the highlights of this outbreak is the enormous complexity and virulence of the infection, it is estimated to be the largest and most harmful so far. In less than ten minutes, 5,000 systems were infected with this fatal malware. Companies such as Mondelez, DLA Piper, Maersk, and banks in Spain, Ukraine, India, Russia, and the United Kingdom, among many others have not been immune to this attack.
As with the recent case of the WannaCry ransomware, the combination of such complex techniques that have been used in the development of this malware is striking. NotPetya not only uses the EternalBlue vulnerability (already used by WannaCry) but also handles others such as theft of memory credentials, permission elevation, etc. The fact that, for the first time in a while, this virus uses an "incubation period" to delay its detection, having more time to spread is very remarkable.
Conclusion:
A lot of these cyber attacks took advantage of old vulnerabilities that would have most likely not been discovered if it weren’t for someone exploiting it. However, This does not mean that we are safe. Cybercrime should be taken seriously and due to our current times’ digitalisation, the risk is even higher. Stay safe out there.
For tips on staying safe, check out the WithYouWithMe Portal, Courses are given for FREE to all ex-military and their families.
